Device Authenticator
SIM-As-An-Identity
Device Authenticator
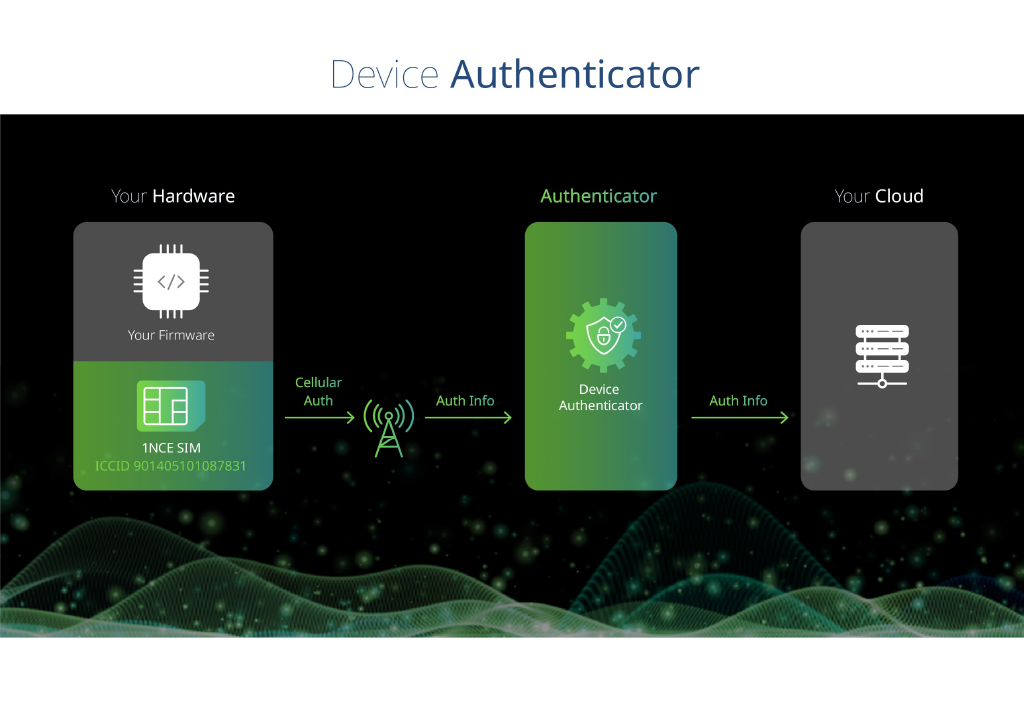
The Device Authenticator offers a secure and automatic onboarding service for devices. The Device Authenticator is based on the Sim-as-an-Identity principle. Through unique identifiers, each SIM Card is securely authenticated and can be immediately used to send data to the device integrator.
Sim-as-an-Identity
The ICCID of the customer SIM is used as a unique identifier for the device.
Updated 2 months ago